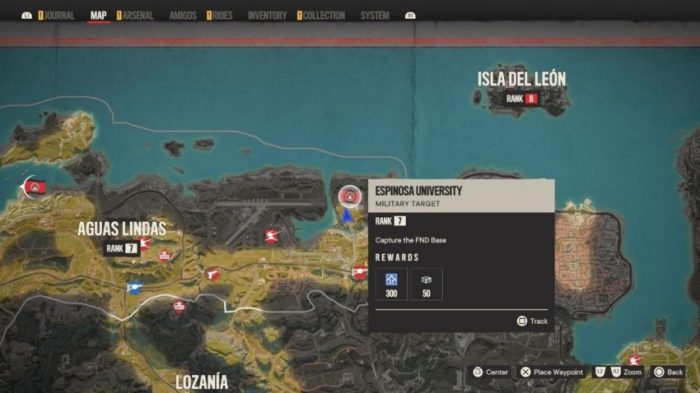
How to capture fnd base – Welcome to the ultimate guide on capturing FND base. In this article, we’ll delve into the fundamentals, methods, protocols, tools, and best practices involved in this critical networking process.
FND base plays a pivotal role in network infrastructure, providing a foundation for various applications and services. Understanding how to capture FND base is essential for network engineers, administrators, and anyone involved in network management.
1. Fundamental Concepts: How To Capture Fnd Base
Capturing FND base is crucial for network infrastructure as it provides a foundation for understanding and managing the network’s behavior. It involves collecting and analyzing data related to the network’s fundamental characteristics, such as traffic patterns, latency, and packet loss.
The underlying principles of FND base capture revolve around the concept of network telemetry, which involves monitoring and measuring network performance metrics. By collecting this data, network administrators can gain insights into the network’s health, identify potential issues, and optimize performance.
FND base plays a vital role in network infrastructure by providing a baseline for comparison and analysis. It allows network administrators to track changes over time, identify trends, and make informed decisions regarding network management.
2. Methods and Techniques, How to capture fnd base

There are various methods and techniques for capturing FND base. One common approach is passive monitoring, which involves using network monitoring tools to collect data without actively interfering with network traffic. This method provides a comprehensive view of the network’s behavior but can be limited by the capabilities of the monitoring tools.
Another method is active monitoring, which involves injecting test traffic into the network to measure performance. This method provides more detailed insights but can impact network performance and is not suitable for all environments.
Each method has its advantages and limitations, and the choice of method depends on the specific requirements and constraints of the network environment.
3. Protocols and Standards

Several protocols and standards are associated with FND base capture. The most common protocol is the Simple Network Management Protocol (SNMP), which provides a standardized framework for collecting and managing network information.
Other protocols include the Internet Control Message Protocol (ICMP), which is used to send error and control messages between network devices, and the Network Time Protocol (NTP), which synchronizes clocks across a network.
These protocols and standards ensure interoperability between different network devices and tools, enabling efficient and consistent FND base capture.
4. Tools and Applications
Numerous tools and applications are available for capturing FND base. These tools provide a range of features and capabilities, from basic monitoring to advanced analysis and reporting.
Some popular tools include Nagios, Zabbix, and PRTG Network Monitor. Each tool has its strengths and weaknesses, and the choice of tool depends on the specific requirements of the network environment.
When selecting a tool, it is important to consider factors such as scalability, ease of use, and support for relevant protocols and standards.
5. Best Practices and Considerations
Effective FND base capture requires careful planning and implementation. Best practices include:
- Establishing clear objectives and identifying the specific metrics to be captured
- Selecting appropriate tools and methods based on network requirements
- Properly configuring monitoring tools to ensure accurate data collection
- Regularly reviewing and analyzing captured data to identify trends and potential issues
Other considerations include:
- The impact of monitoring on network performance
- Data storage and retention policies
- Security measures to protect captured data
Essential FAQs
What is the significance of capturing FND base?
Capturing FND base provides valuable insights into network traffic patterns, performance metrics, and potential issues. It enables network engineers to troubleshoot problems, optimize resource allocation, and improve overall network efficiency.
What are the different methods for capturing FND base?
Common methods include passive sniffing, active probing, and flow monitoring. Passive sniffing involves listening to network traffic without interfering, while active probing involves sending packets to elicit responses from devices. Flow monitoring tracks the flow of packets over time, providing a comprehensive view of network traffic.
What protocols are associated with FND base capture?
Relevant protocols include TCP, UDP, ICMP, and IP. These protocols provide the underlying mechanisms for data transmission and communication between devices on a network.