Get a server IP address and unlock the gateway to your server. This comprehensive guide will equip you with the knowledge and tools to obtain, understand, and manage IP addresses, empowering you to establish secure and efficient connections.
Delving into the intricacies of IP addresses, we’ll explore their types, structure, and assignment, providing a solid foundation for navigating the digital landscape.
Finding IP Address
Obtaining a server’s IP address is crucial for various purposes, including network management, troubleshooting, and security analysis. There are several methods to acquire this information, each with its advantages and limitations.
Command-Line Tools, Get a server ip address
- ifconfig (Linux/macOS):Displays network interface information, including IP addresses.
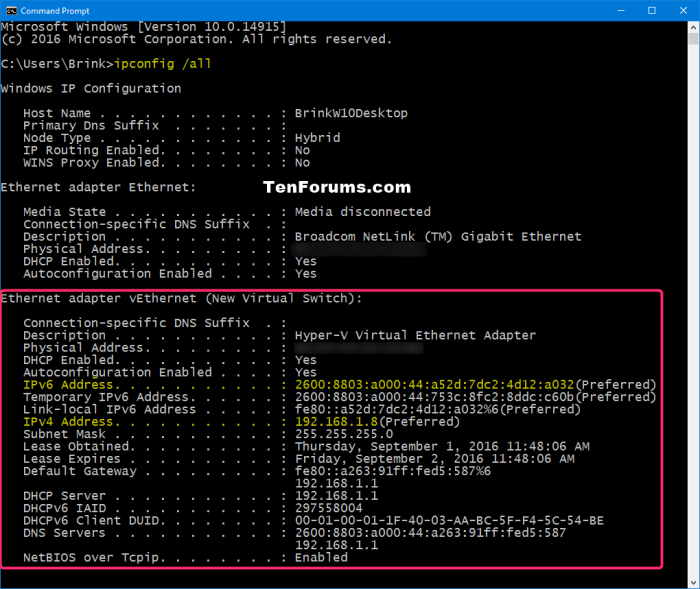
- ipconfig (Windows):Similar to ifconfig, it provides IP address details for network adapters.
- nslookup (Windows/Linux/macOS):Can be used to resolve domain names to IP addresses and vice versa.
Online Services
- IP Address Lookup Tools:Websites like WhatIsMyIP.com and IPChicken.com provide simple interfaces to retrieve your IP address.
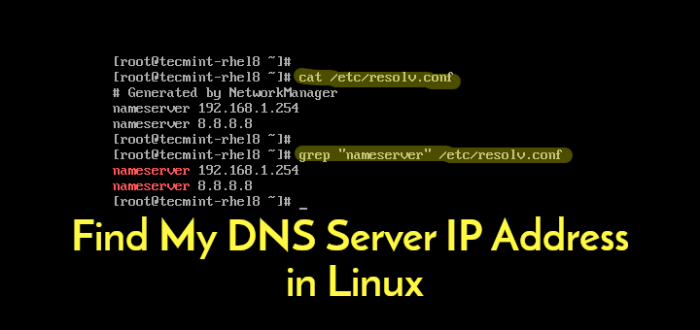
- DNS Lookup Services:DNS (Domain Name System) servers can resolve domain names to IP addresses. You can use online DNS lookup tools or command-line utilities like dig or nslookup.
Types of IP Addresses
IP addresses are categorized into two main types: IPv4 and IPv6.
IPv4
IPv4 (Internet Protocol version 4) is the most widely used IP address format. It consists of 32 bits represented as four octets (numbers) separated by periods, e.g., 192.168.1.1.
IPv6
IPv6 (Internet Protocol version 6) is the successor to IPv4, designed to address the exhaustion of IPv4 addresses. It uses 128 bits represented as eight groups of hexadecimal digits separated by colons, e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
IP Address Structure: Get A Server Ip Address
IP addresses are structured according to specific rules and conventions.
Octet Structure

IPv4 addresses are divided into four octets, each representing a range of values from 0 to 255. The octets are written in decimal notation, separated by periods.
Hexadecimal Notation
IPv6 addresses are written in hexadecimal notation, using 16-bit hexadecimal digits (0-9, A-F). The digits are grouped into eight 16-bit segments, separated by colons.
IP Address Assignment
IP addresses are assigned to devices by network administrators or Internet Service Providers (ISPs). They can be static (permanently assigned) or dynamic (assigned temporarily).
IP Address Lookup

IP address lookup is the process of obtaining information about a server or device based on its IP address.
DNS Lookup
DNS (Domain Name System) is a distributed database that translates domain names (e.g., google.com) to IP addresses. DNS lookup tools allow you to query DNS servers to resolve IP addresses.
whois

whois is a protocol and database used to query information about domain names and IP addresses. whois queries can provide details such as the domain’s owner, contact information, and registration history.
IP Address Security
IP addresses are important security considerations.
IP Address Spoofing
IP address spoofing is a technique where an attacker disguises their IP address as another device’s IP address. This can be used to gain unauthorized access to networks or systems.
IP Address Blacklisting
IP addresses can be blacklisted if they are associated with malicious activity. Blacklisted IP addresses may be blocked from accessing certain networks or services.
Protecting Against IP Address Threats
To protect against IP address threats, consider implementing measures such as firewalls, intrusion detection systems (IDS), and IP address monitoring tools.
Question & Answer Hub
How can I find the IP address of my server?
Utilize command-line tools like “ifconfig” or “ipconfig” or employ online services such as “whatismyipaddress.com”.
What are the different types of IP addresses?
IPv4 and IPv6 are the most common types, with IPv4 using 32-bit addresses and IPv6 utilizing 128-bit addresses.
How do I protect against IP address spoofing?
Implement strong firewall rules, use intrusion detection systems, and configure your network devices to prevent unauthorized access.